5 Ways AI in Industrial Automation is Powerfully Transforming the Future of Manufacturing
Introduction: AI in Industrial AutomationImagine a factory where systems anticipate failures, robot arms collaborate seamlessly with human operators, and digital twins simulate real-world changes before they happen. That’s the power of ai in industrial automation—a fusion of artificial intelligence and automation reshaping industries. In this deep-dive, we’ll explore how this technology works, who’s leading the […]
The Ultimate Guide to Using a YouTube Title Generater for Maximum Views
Introduction: Why Your YouTube Title Matters More Than Ever On YouTube, the difference between a video that explodes with views and one that gets lost in the algorithm often comes down to one simple element: the title. A compelling, keyword-rich, and curiosity-driven title can skyrocket your click-through rate (CTR), while a vague or generic one […]
Best Android Box for Television in 2025: 9 Top Picks for Every Budget
Introduction: Why an Android Box for Television Is the Upgrade You Need Streaming has reshaped the way we consume content. From Netflix marathons to YouTube tutorials, the TV has become the centerpiece of our digital life — but not all TVs are equally smart. That’s where an android box for television comes in. These compact […]
Malware/win.generic.c5762214 – Detection, Removal & Threat Analysis (2025 Guide)
Cybersecurity threats are evolving rapidly, and among the rising dangers is a particularly stealthy malware variant known as malware/win.generic.c5762214. In this comprehensive guide, we’ll explore what it is, how it operates, how to detect and remove it, and the best tools for prevention and analysis. 🔍 What Is malware/win.generic.c5762214? The term malware/win.generic.c5762214 is a generic […]
Zeus Trojan Malware: Evolution, Impact & Defense—A Comprehensive Guide
Introduction: Understanding zeus trojan malware First detected in 2007, zeus trojan malware—also known as Zbot—has become a notorious banking Trojan that has forged a legacy through widespread financial theft and extensive botnet operations Wikipedia. This malware has evolved into multiple variants over the years, affecting countless individuals and institutions worldwide. In this guide, you’ll uncover […]
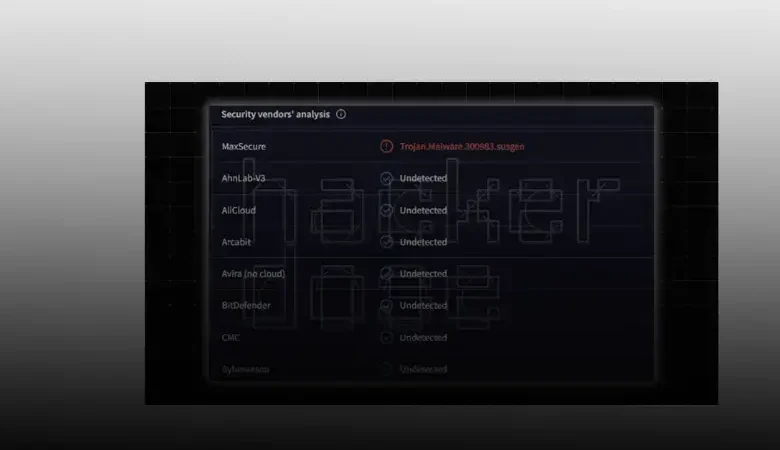
Trojan.Malware.300983.Susgen: What It Means and How to Handle It Safely
Introduction: Understanding Trojan.Malware.300983.Susgen If you’ve ever received an antivirus alert labeled trojan.malware.300983.susgen, you’re not alone. This detection, especially from MaxSecure, often triggers panic—but as many community reports show, it’s frequently a false positive. In this guide, we’ll explain what trojan.malware.300983.susgen is, how it’s detected, and how to remove it safely—without causing unnecessary harm to legitimate […]
NICE Challenge Malware Aftermath Cleanup: Expert Guide & Real-World Strategies
Introduction Cybersecurity simulations, like the NICE Challenge Project, play a vital role in preparing professionals for real-world digital threats. One of the most revealing and skill-testing simulations is the NICE Challenge malware aftermath cleanup. This challenge tasks participants with identifying, assessing, and removing sophisticated malware from compromised systems—skills critical in today’s threat landscape. In this […]
Hello