5 Key Insights About West Virginia Traffic Cameras: What You Need to Know
Traffic cameras have become an essential part of road safety and law enforcement across the United States. In West Virginia, these devices play a significant role in monitoring traffic flow, ensuring safety, and even generating revenue for local governments. With technology advancing rapidly, many are wondering how effective these cameras truly are, whether they are […]
10 Essential Insights About Woodland Park Traffic Cameras for Safer Roads
Efficient traffic management is crucial for maintaining safety and convenience on the roads. Woodland Park traffic cameras play a pivotal role in achieving this goal by providing real-time traffic updates, ensuring road safety, and aiding urban planners. In this article, we delve into the key aspects of Woodland Park traffic cameras, exploring their benefits, functionality, […]
How to Block Ping Requests in Linux
Ping requests, commonly referred to as ICMP Echo Requests, are a basic diagnostic tool used to test network connectivity. However, leaving your system open to these requests can expose it to network threats, such as Distributed Denial-of-Service (DDoS) attacks. Blocking ping requests in Linux is a vital step for enhancing system security. In this article, […]
How to Block Ping Requests: A Comprehensive Guide
In the realm of network security and performance optimization, how to block ping requests is an essential measure. Ping requests, also known as ICMP Echo Requests, are often used for network troubleshooting. However, they can also be exploited in denial-of-service (DoS) attacks or other malicious activities. This article provides a detailed guide on how to […]
Ultimate Guide to Logitech Cordless Devices for Windows 10
Logitech has long been a trusted name in computer peripherals, offering a wide range of logitech cordless devices for windows 10 that enhance productivity and provide superior functionality. If you’re a Windows 10 user, integrating Logitech cordless devices into your setup can significantly improve your experience. This guide explores the best Logitech cordless devices, compatibility […]
Comprehensive Guide to Multiple Wire Bond Pads
In the realm of microelectronics, multiple wire bond pads play a pivotal role in ensuring seamless connectivity between integrated circuits (ICs) and their packaging. As advancements in semiconductor technology continue to push the boundaries of miniaturization, the need for efficient and reliable wire bonding solutions has become increasingly critical. This article delves deep into the […]
Comprehensive Guide to Multiple Wire Bond in Same Pads
Multiple Wire Bond in Same Pads, in the field of microelectronics, wire bonding serves as a pivotal process for establishing electrical connections between the silicon chip and its external circuits. As the industry evolves, leveraging multiple wire bonds in the same pad is emerging as a highly efficient approach to enhance functionality and reliability in […]
What Does PAC Stand for in Steering Wheel Control?
In the automotive world, steering wheel control systems play a significant role in enhancing convenience and safety while driving. The term PAC, frequently associated with these systems, often raises questions among car enthusiasts and everyday users alike. This article aims to provide an in-depth explanation of what PAC stands for, its relevance in steering wheel […]
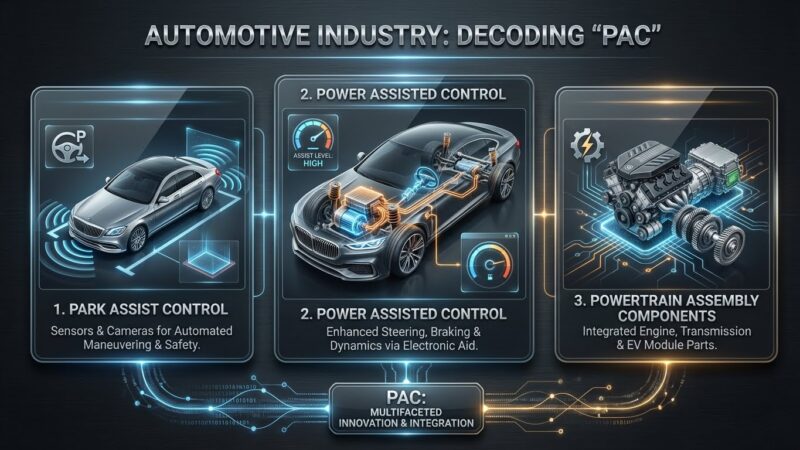
What Does PAC Stand for in the Automotive Industry?
Introduction Ever wondered what does PAC stand for in the automotive industry? If you’re curious about automotive systems, you’ve likely heard this term before. PAC, short for Primary Air Control, plays a crucial role in modern vehicles. It’s a system designed to optimize air intake, regulate emissions, and improve fuel efficiency. Let’s dive deeper into […]
Guide 1995 corvette passive keyless entry
The 1993–1996 keyless entry Chevrolet Corvette C4 models introduced several technological advancements, 1995 corvette passive keyless entry, one of the most notable being the passive keyless entry (PKE) system. This innovative feature allowed owners to lock and unlock their vehicles without pressing a button, relying instead on proximity-based radio frequency (RF) communication between the car […]
Hello